Transitioning from Hybrid Identity to Full Cloud-Only Identities with Entra ID
A common scenario organizations often ask of me, “is how to break hybrid identity from Windows Active Directory and utilize Entra ID as their single identity provider (IDP).” As organizations increasingly move towards cloud native solutions, the need to transition from hybrid identity setups to full cloud-only identities becomes even more desirable. For companies considering this journey, the below image represents a high-level view of what the migration from Windows Active Directory to Microsoft Entra ID looks like.
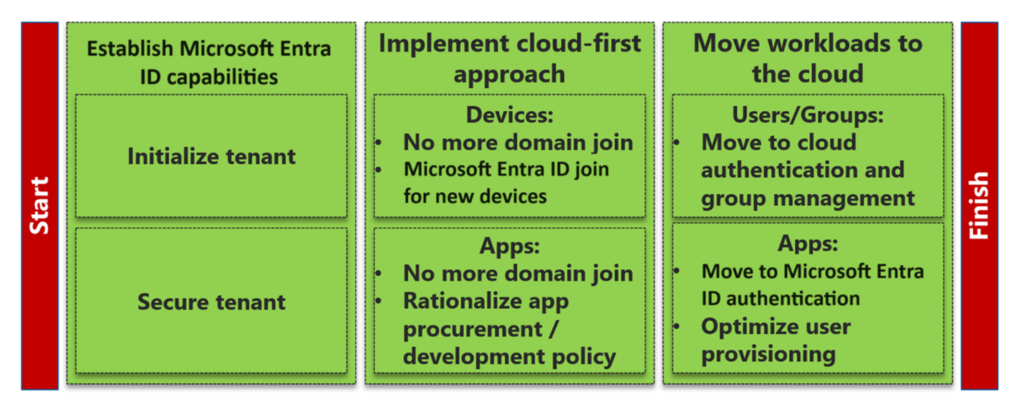
Why Transition to Full Cloud-Only Identities?
Transitioning to full cloud-only identities offers several benefits, including simplified identity management, enhanced security, support for modern authentication protocols, and improved user experience. By leveraging Entra ID, organizations can streamline their identity and access management processes, reduce reliance on on-premises infrastructure, and enable seamless access to cloud-based applications and services.
Key Considerations and Checklist
-
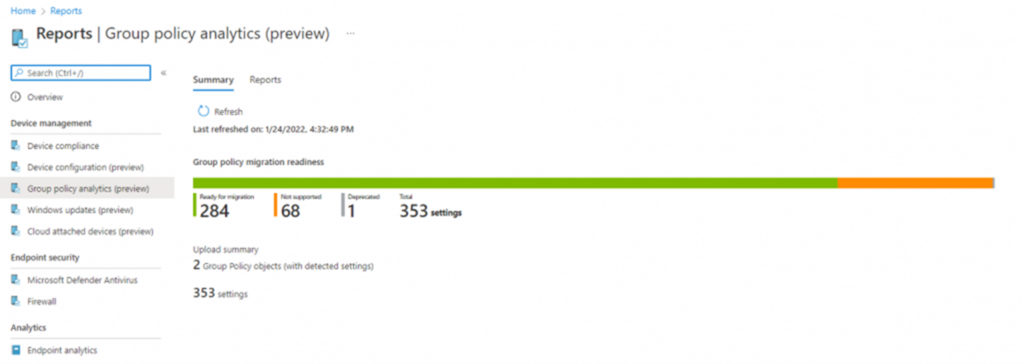
Analyze and Migrate Group Policy Objects (GPOs)
- Utilize Group Policy Analytics to identify which settings from your GPOs can be migrated to native MDM settings within InTune. Review and determine the applicability of these settings to Entra ID joined devices. For example, settings like “Domain member: Require strong session key” may no longer be necessary.
- You may also want to consider implementing the Security Baseline for Windows 10 and later and use the Settings Catalog to layer on additional required settings.
-
Ensure Applications are Cloud-Based
- Verify that your applications have been added to the Entra ID app gallery, enabling Single Sign-On (SSO) for users on Entra ID joined devices without additional configuration.

-
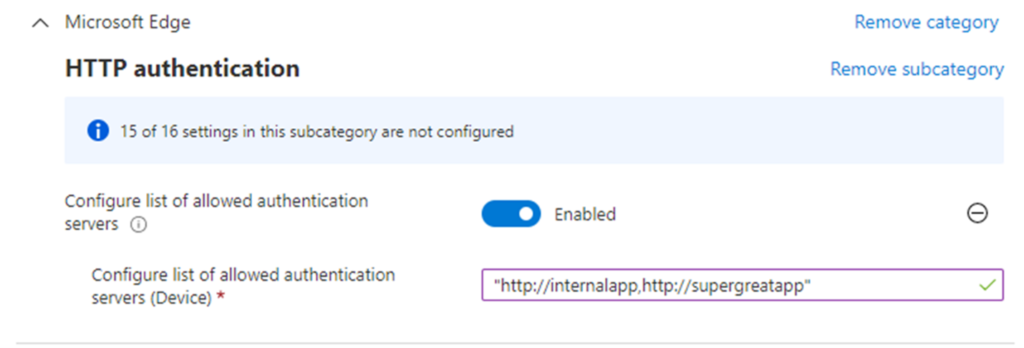
Add On-Prem Web Apps to Browser’s Trusted Sites
- For on-prem web apps, add them to your browser’s trusted sites list using policies like AuthServerAllowList in Microsoft Endpoint Manager. This enables Windows integrated authentication and provides an SSO experience for on-prem apps.
- If you need to access these webapps off the corporate network, then Entra ID App Proxy may be required.
-
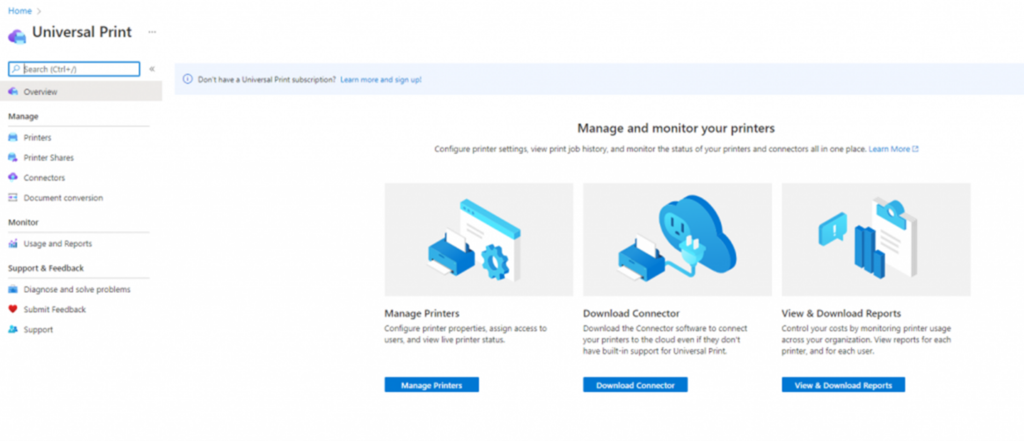
Integrate Printers with Universal Print
- Implement Universal Print for modern print management, allowing printers to communicate directly with Azure. This eliminates the need for managing print drivers and supports a wide range of printers.
-
Review Reliance on RADIUS Authentication for Network Access
- Entra ID joined devices don’t natively support RADIUS authentication which can present a challenge for Wi-Fi and VPN connectivity because a RADIUS server requires a computer object in AD. The recommended approach for Entra ID joined devices is to use SCEP or PKCS certificates for Network authentication and for VPN scenarios leverage SSO with Entra ID.
-
Plan for File Shares
- Determine where file share data will reside once Windows AD is removed. Leverage a mix of SharePoint, Teams, OneDrive, and Azure Storage Accounts based on collaboration and security needs.
-
Decommission Hybrid-Exchange
- Decommissioning the on-prem exchange management server cannot be done until AD Sync has been disabled on the tenant. Before decommissioning hybrid exchange, consider migrating any resources that may be left on-prem such as legacy public folders or if the Exchange server is being used for SMTP relay.
-
Set Up SQL Entra ID Integrated Authentication
- Remove any SQL dependencies on AD by setting up integrated Entra ID authentication for SQL. Validate and remove dependencies on domain service accounts used for tasks like SQL Jobs.
Handling Device Migration from Domain-Joined to Entra ID Joined Devices
Migrating devices from domain-joined to Entra ID joined, requires careful planning to minimize disruption and ensure a smooth transition. Here are the key steps and considerations.
-
Assess Device Readiness
- Ensure that devices are running Windows 10 or Windows 11, as these are compatible with Entra ID joining.
- Check the current state of devices using the dsregcmd /status command to determine if they are domain-joined, hybrid joined, or Entra ID joined.
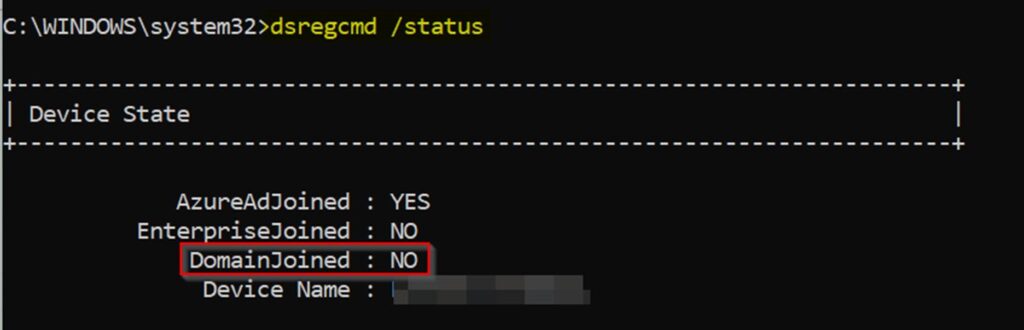
-
Unjoin and Rejoin Devices
- Hybrid Entra ID joined devices cannot be directly converted to Entra ID joined. They must be removed from the Windows AD Domain and then added back to Entra ID.
- Manually unjoin devices by running the command prompt as administrator and execute the command dsregcmd.exe /debug /leave
- Rejoin devices to Entra ID using the appropriate enrollment methods, such as Autopilot or Intune.
-
User Profile Migration
- Ensure proper backups of end-user data before proceeding with the migration such as copying important local data to OneDrive.
- Consider leveraging tools like ProfWiz to streamline the conversion of user profiles from AD to Entra ID profiles on devices.
-
Minimize User Disruption
- Consider phasing out hybrid Entra ID joined devices during a hardware refresh cycle to avoid significant disruptions to end-user workflows.
- Communicate the migration plan and provide support to users throughout the process to address any issues that may arise.
Final Thoughts
Transitioning from hybrid identity to full cloud-only identities with Entra ID requires careful planning and a shift in mindset. While this transformation offers numerous benefits, it may not be feasible for all businesses immediately. Organizations who are heavily reliant on on-prem infrastructure should first consider modernizing their network environment by moving applications to cloud native solutions that support modern authentication protocols, while slowly removing dependencies on Windows Active Directory and legacy authentication methods such as LDAP and Kerberos.
I hope this article can serve as a starting point to help you with the initial planning towards making the move to cloud-only identities For anyone who has gone through this transition or is currently considering this I would love to hear about it!
Until next time!